"In 2022, the average cost of a data breach in the US was $9.48 million. Don't let IAM mismanagement contribute to your expenses." — IBM's Cost of a Data Breach Report
When it comes to AWS cloud infrastructure, the lurking dangers often resemble the metaphorical "dead bodies" scattered across your cloud environment. In AWS, these are often unused cloud identities (AWS IAM roles, users, groups), permissions (like iam:CreateRole), and credentials (such as IAM user access keys and console passwords). And just like you wouldn't leave "dead bodies" unaddressed, these unused elements should be managed to maintain a secure and efficient cloud environment.
The Problem with Existing CSPM/CIEM Tools
Most Cloud Security Posture Management (CSPM) and Cloud Infrastructure Entitlement Management (CIEM) solutions provide a limited solution. These tools claim to handle "entitlement management" but stumble on the management part. Here's the reality:
- These tools are primarily designed and used by security teams, alienating developers and DevOps from the process.
- Security teams are often hesitant to press that "Remove" button for unused permissions for fear of unilaterally and inadvertently taking down a production service.
- Existing solutions don't offer a mechanism to restore permissions or identities, making security measures a one-way street.
Noq: A Different Approach to CIEM
We've been listening, and we built something that aims to change how you look at CIEM, especially in AWS environments. Our approach is built around IAMbic, an open-source engine that treats IAM as version-controlled code. Learn more about IAMbic on GitHub and join us on Slack for help.
Why IAMbic?
- Unified View: IAMbic integrates with AWS, Okta, Azure AD, and Google Workspace (More coming soon). It offers a consistent and unified view in human-readable YAML files.
- Version Control: All IAM changes triggers a git commit, enabling a granular audit trail.
- Bi-Directional Management: IAMbic templates can write IAM changes back to the cloud through your CI/CD pipeline, simplifying management tasks.
What Sets the Noq Platform Apart?
1. Automatic and Gradual Cleanup
One of Noq’s core features is its ability to automatically and gradually clean up your AWS environment via pull requests to your IAMbic templates repository. You can specify the number of risky, unused identities, cloud credentials, and permissions you want to address within a given time frame.
These pull requests can be directly assigned to the identity owners for review and approval. If the pull request remains unmerged after a set period, you can configure Noq to either auto-approve and merge the request or close it, depending on your risk tolerance. This allows you to clean dead bodies up in a sustainable, manageable, and auditable way.


2. Risk-Adjusted Suggestions
Noq doesn't just flag unused permissions; it analyzes the risk associated with each. Noq's findings dashboard enables you to visualize your AWS environment's security posture over time. Uncover not just what's unused, but also what actually poses a potential threat. We prioritize your work by displaying the unused actions or identities that pose the most risk first.

3. In-Depth Context
Dive deeper into each identity or permission. Review all unused actions, their last usage, and the risks associated with each.

4. Dismiss Non-Risky Elements
Some elements may be unused but are essential. For example, an SRE team might have emergency production access that is rarely used. With Noq, you can dismiss these findings as per your organizational context, and keep your dashboards displaying only relevant and actionable issues.

5. Tailored Remediation
Choose between remediation through IAMbic pull requests or via JIRA tickets for your developers. Your call. Developers have detailed instructions about how to resolve a finding, complete with examples in Terraform, CloudFormation, and JSON.
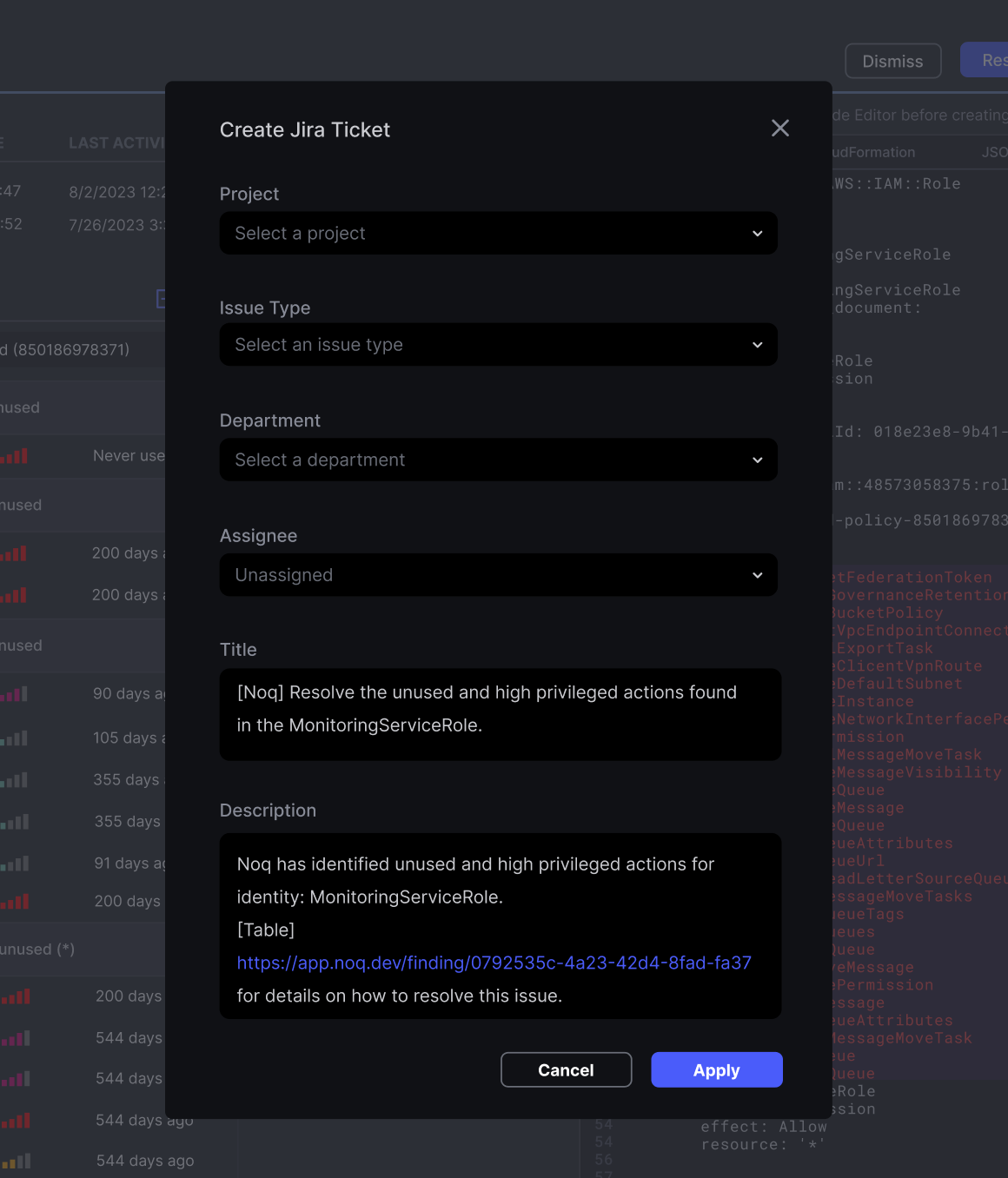
6. Easy Reversion
Worried about losing something important? If a remediation is done through IAMbic, a simple click of the "Revert" button for the request in the Noq Platform can bring back the deleted permissions.
7. Paved Road Experience
We believe you can't reasonably remove permissions without providing an easy way to get them back. Noq offers a self-service click-through workflow for your end-users, allowing users to request permissions through a streamlined workflow, eliminating the back-and-forth between developers, DevOps, and security teams.
IAMbic: Version Control for IAM
IAMbic is more than an auditing tool; it's designed for DevSecOps, Security, and Compliance teams. IAMbic uses Git as a database to represent your IAM permissions. and allows you to be as hands-on or as hands-off as you'd like. Temporary access or permissions can be easily managed, and expiration of access rules and permissions are handled automatically.
For more on IAMbic, check out the Quick Start Guide
Integrating Noq and IAMbic
The Noq Platform only requires read-access to your AWS environment and seamlessly integrates with IAMbic, offering a comprehensive solution. Noq offers self-service access and permissions workflows, temporary Just-In-Time (JIT) credentials, and removal of unused access/permissions/credentials/identities within your cloud environment.
Closing Thoughts
Effective Cloud Infrastructure Entitlement Management is not a one-team game. It requires flexibility and collaboration among different internal stakeholders - Developers, DevOps/SRE, and Security. The Noq Platform, backed by IAMbic, is designed to be the tool that integrates with your existing workflow to make this easy.
So why let dead bodies fester when you can clean them up effectively? Welcome to a new age of AWS security management—where there are fewer "dead bodies," and a continuously secure and efficient cloud posture.
Ready to experience next-level AWS security for yourself? Schedule an exclusive demo on our website. For the open-source enthusiasts among you, dive into IAMbic directly on our GitHub Repository. Got questions or need support? Our dedicated team is just a Slack message away—join our Noq Community on Slack for real-time assistance.
.webp)


